Exploring the Key Types of Penetration Testing in Cybersecurity
In today’s rapidly evolving threat landscape, organizations must do more than just deploy firewalls and antivirus software—they need to think like attackers. That’s where penetration testing (pentesting) comes in.
A penetration test emulates real-world attacker techniques to uncover vulnerabilities that may threaten the confidentiality, integrity, or availability of critical systems. By identifying and addressing these weaknesses proactively, organizations can strengthen their defenses and reduce the risk of exploitation.

Asman
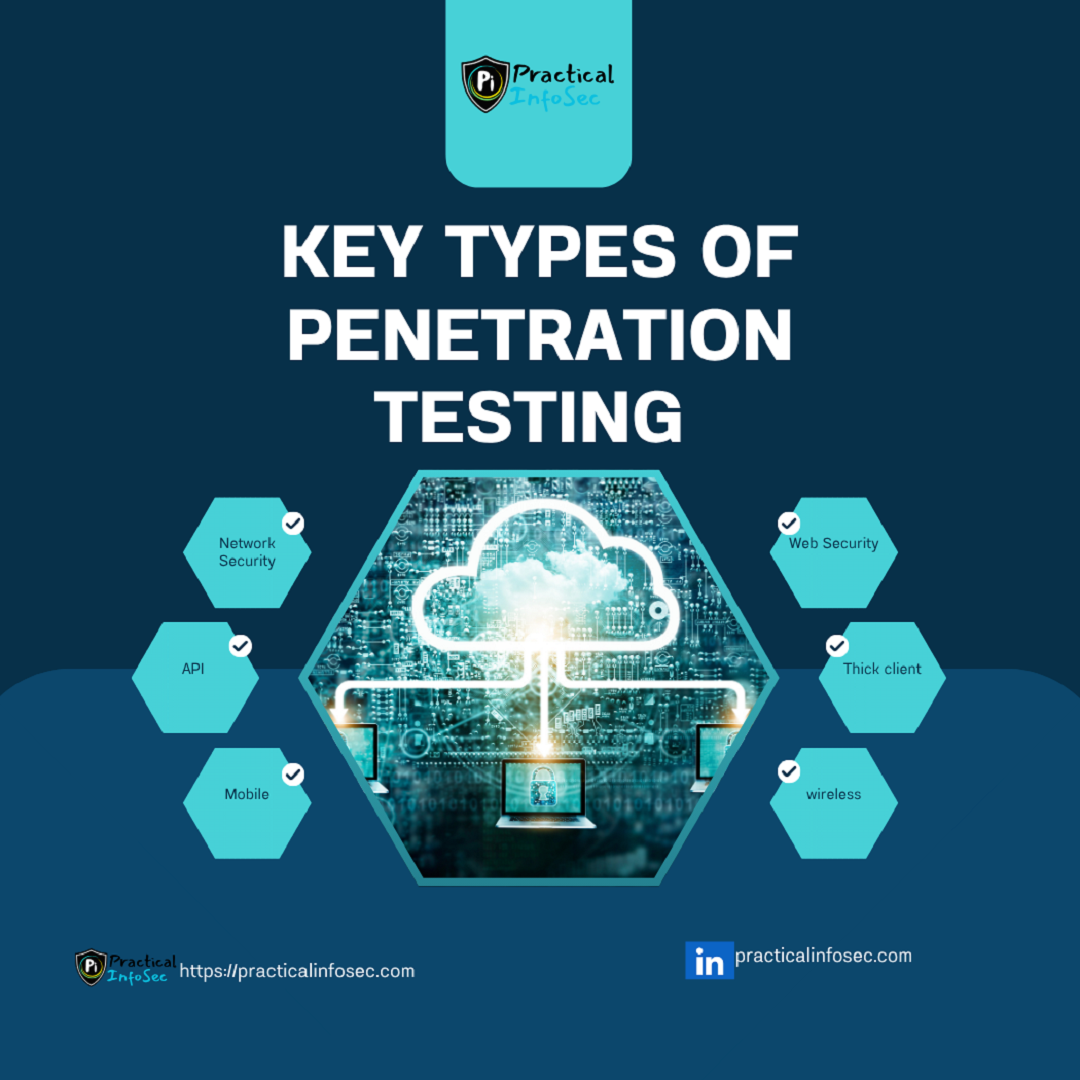
The scope of a pentest varies depending on specific goals. Some tests focus on external infrastructure—such as internet-facing servers and services—while others dive into internal corporate networks, web applications, APIs, or mobile environments. Each type offers a unique lens into the organization’s security posture.
In this article, we’ll explore the different types of penetration testing, when they’re used, and why each one plays a vital role in protecting modern digital assets.
Penetration Testing: Staying Legal and Ethical
Penetration testers must operate within ethical boundaries, securing written authorization and following clearly defined rules of engagement. Non-disclosure agreements (NDAs) safeguard the interests of both the client and the tester. Since legal requirements and compliance standards differ across regions, it's crucial to verify what activities are legally permitted before beginning any assessment.
The Role of Penetration Testing
Penetration testing plays a crucial role in a comprehensive security program by revealing how vulnerabilities can be exploited in real-world scenarios. It complements other practices like vulnerability scanning, code reviews, and compliance audits. Pentest results help assess risk more accurately, verify the effectiveness of security patches, and support informed decision-making for future security investments.
Different Types of Penetration Testing
1. Web application penetration testing:
Web Application Penetration Testing is a critical process in identifying and exploiting vulnerabilities within web applications to assess their security posture. This type of testing simulated real-world attacks to uncover weakness such as SQL Injection, Cross-Site Scripting (XSS), Local File Inclusion (LFI), and others that could be exploited by malicious attacks. Penetration tester use a combination of automated tools and manual techniques to probe the application for vulnerabilities, validate their impact, and suggest mitigation strategies. By performing these tests, organizations can identify potential security flaws before they are exploited by attackers, ensuring the integrity and confidentiality of sensitive data and safeguarding the application from future threats.
Most common attacks in web applications
- Broken access control
- Cryptographic failures
- Injection flaws (XSS, SQL, SSTI, etc.)
- Insecure design
- Security misconfiguration
- Vulnerable and outdated components
- Identification and authentication failures
- Software and data integrity failures
- Lack of logging and monitoring
- Server-Side Request Forgery (SSRF) vulnerabilities
2. Mobile penetration testing:
A mobile application penetration test includes a static analysis and a dynamic analysis of the application, in addition to the tests carried out on the servers and, possibly, the APIs.
On the one hand, static analysis involves extracting elements (meta-information and source code, for example) to carry out reverse engineering attempts. On the other hand, dynamic analysis involves looking for vulnerabilities in the application during use (runtime). In general, in the event of misconfiguration or faulty implementation, it is possible to bypass controls or extract data.
As there is a steady growth in mobile devices, Android and iOS penetration testing is carried out in a streamlined manner. The app’s functionality is disrupted or access to sensitive data is gained through this testing method.
Most common attacks in Mobile penetration testing
- Improper Credential Usage
- Inadequate Supply Chain Security
- Insecure Authentication/Authorization
- Insufficient Input/Output Validation
- Insecure Communication
- Inadequate Privacy Controls
- Insufficient Binary Protections
- Security Misconfiguration
- Insecure Data Storage
- Insufficient Cryptography
3. API penetration testing:
An API (Application Programming Interface) is a set of rules that allows different software systems to talk to each other and share data. API testing involves checking how the API functions, whether it can be misused, and if security features like authentication and authorization can be bypassed. Testers also look for issues like command injection or SQL injections, and whether the API responses display sensitive data on a web page. The goal is to find any security weaknesses in the API itself or how it is used in an application.
Most common attacks in API penetration testing
- Broken Object Level Authorization (BOLA)
- Broken Authentication
- Broken Object Property Level Authorization (BOPLA)
- Unrestricted Resource Consumption
- Broken Function Level Authorization
- Unrestricted Access to Sensitive Business Flows
- Server Side Request Forgery (SSRF)
- Security Misconfiguration
- Improper Inventory Management
- Unsafe Consumption of APIs
4. Network penetration testing:
Network penetration testing uncovers security weaknesses in network infrastructure—such as firewalls, switches, routers—and endpoint devices. It helps prevent threats like firewall misconfigurations, attacks on network devices, DNS exploits, proxy abuse, and man-in-the-middle (MiTM) attacks.
These tests involve techniques like port scanning, system fingerprinting, configuration analysis, malware and virus detection, and traffic fuzzing and known vulnerable component exploitation.
Most common attacks in Network penetration testing
- Open Ports & Unfiltered Services
- Default Credentials / Weak Passwords
- Unpatched Software & OS Vulnerabilities
- Misconfigured Firewalls & ACLs
- Lack of Network Segmentation
- Unencrypted Protocols
- DNS and DHCP Attacks
- SNMP Enumeration & Misconfigurations
- Man-in-the-Middle (MitM) Opportunities
- SMB/NetBIOS Issues
5. Thick Client penetration testing:
Thick client applications, also known as desktop applications, are fully functional computing systems that operate independently while connected to a network. Unlike thin clients, which rely heavily on a central server and often lack features like local storage, thick clients can function with or without network connectivity. Thick client penetration testing is the process of evaluating the security of these applications by identifying vulnerabilities, testing authentication controls, analyzing data encryption, checking for misconfigurations, and inspecting network communication. The goal is to ensure the application is secure, robust, and resistant to potential threats.
Few examples of thick client applications are Spotify, outlook, ERP Software, skype, Notepad++, Firefox.
Most common attacks in Think Client penetration testing
- Improper Authentication & Authorization
- Insecure Data Storage
- Insecure Deserialization
- Insecure Communication (Lack of Encryption / TLS)
- Reverse Engineering & Binary Manipulation
- Unvalidated Input / Injection Attacks (SQLi, Command Injection, etc.)
- Insecure Inter-Process Communication (IPC)
- Business Logic Vulnerabilities
- Security Misconfigurations
- Use of Vulnerable Third-Party Components

Penetration Testing Approaches
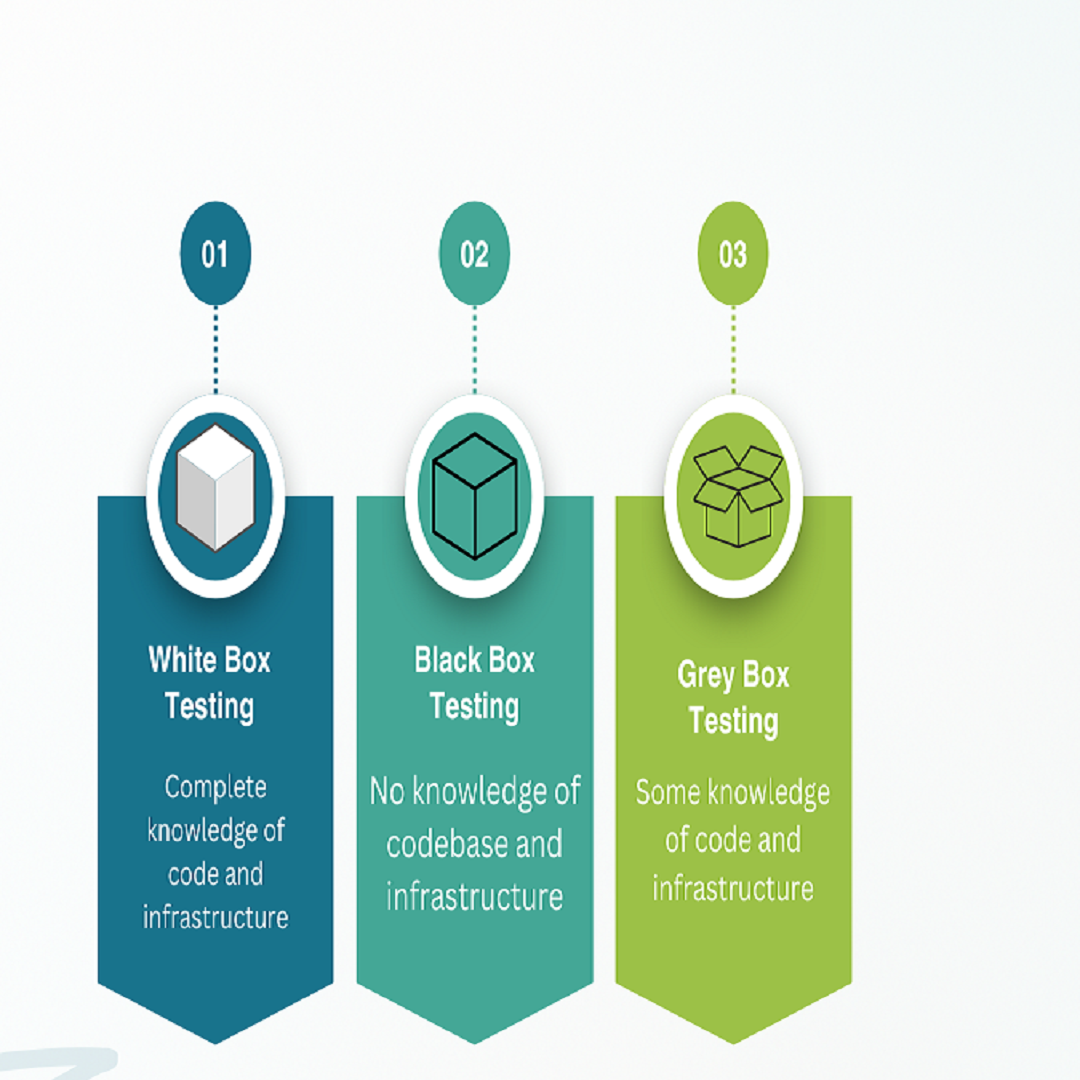
1. White Box Testing
White Box Testing is a software testing technique where the tester has full access to the application's internal code, logic, and architecture. It allows security professionals and developers to design test cases based on how the system is built, making it ideal for uncovering vulnerabilities like logic flaws, insecure data handling, and broken authentication mechanisms.
2. Black Box Testing
Black box tests are done without knowing or understanding the internal mechanism of the software. Black box testing is the most widely used testing method. The tester does not know the software and designs the test as an uninformed attacker. Black box testing focuses on the functionality of the software. It is usually done at the requirements or specification level.
3. Grey Box Testing
Often enough, a web application involves authentication and authorization components. To be able to test these, we request for a dummy user account with the least level of privileges within the application. Using this account, we can log in and test for various flaws in the authentication scheme, as well as attempt to escalate our privileges and bypass authorization restrictions.