Secure Session Management: Best Practices & Techniques
Session management is vital for maintaining secure and reliable user authentication in web applications. This guide covers essential best practices and techniques to prevent session-related threats like hijacking and fixation.

Asman
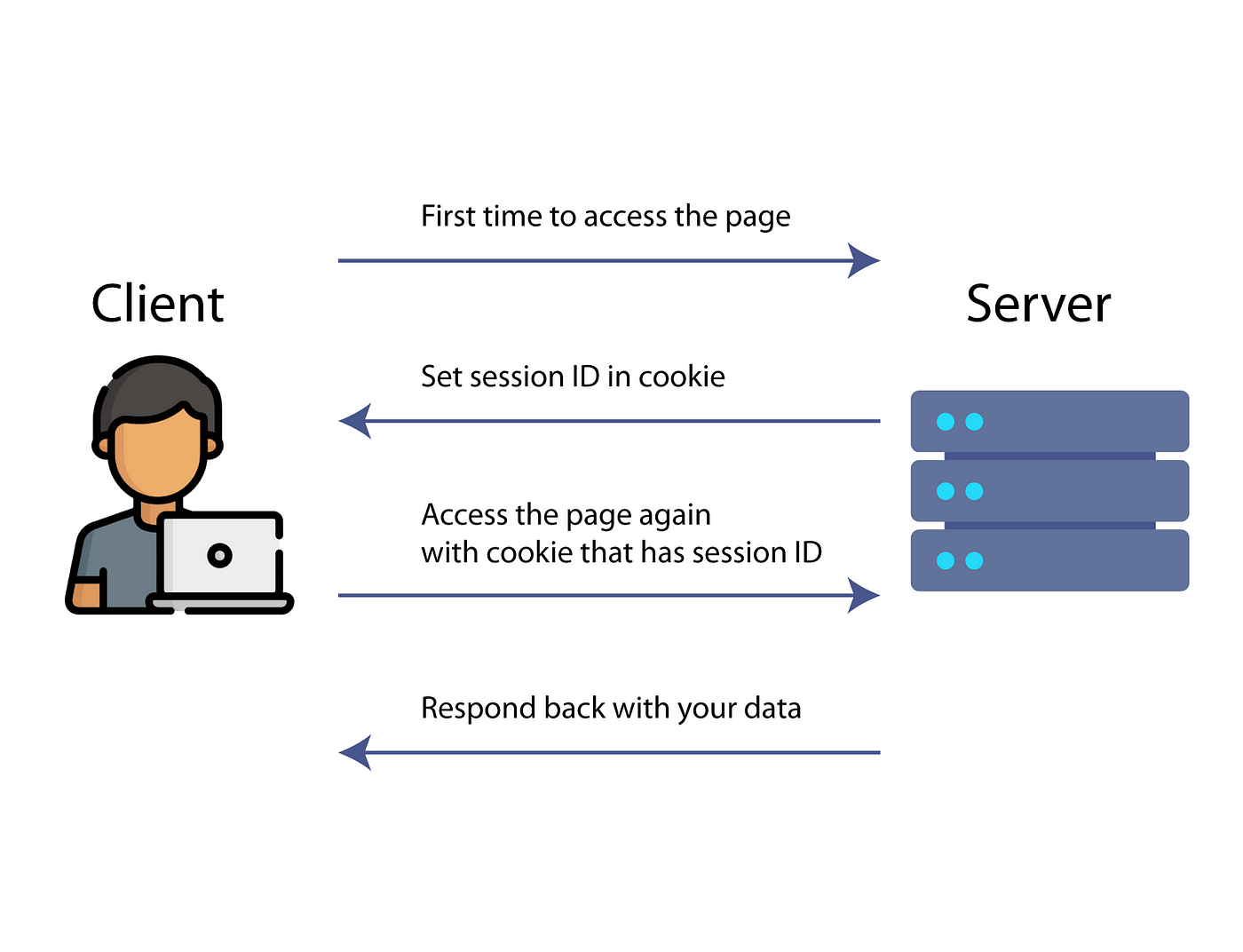
Session is nothing but a server side storage of users information to persist the activity with the web site. Usually all the servers generates a session for that connection with unique session token which is known as Session ID. Do make a note, Session values should be stored server side but not client side. For example whenever you login to website, the server will store your information in your system as a cookie. These cookies will help in authenticity. Since server generated a session ID for a user, client doesn’t need to provide his information on every subsequent requests. Client (browser) usually store and send the token as a cookie to the server. When user clicks on Logout link, the cookie having session ID would be deleted and server will terminate the user’s activity.
Session management refers to controlling user interactions within a web application, including login, access rights, and session timeout. After a user logs in, a session token is created to track their activity, typically saved as a cookie in the browser.
What Are Cookies?
Similar to Session, cookie also store the data on the client’s computer. Cookies are created when you use your browser to visit a website that uses cookies to keep track of your movements within the site, help you resume where you left off, remember your registered login, theme selection, preferences, and other customization function Session Management: Storing session IDs to maintain user sessions.
Cookies Attributes :
- Secure
- Domain
- Path
- HTTPOnly
- Expires
- Max-Age
- SameSite
Secure Attribute :
Cookies with the Secure attribute are only sent over an encrypted connection (HTTPS).
Privilege Escalation
This vulnerability occurs when an attacker is able to exploit a bug or design flaw in an application to gain access to resources or functionality that should be restricted to higher-privileged users. This can involve either Vertical Privilege Escalation (e.g., a normal user gaining administrative privileges) or Horizontal Privilege Escalation (e.g., a user gaining access to another user’s resources at the same privilege level).
Domain :
‘Domain’ attribute specifies the domain for which the cookie is valid and can be submitted with every request for this domain or its subdomains. If this attribute is not specified, then the hostname of the originating server is used as the default value.
Path :
The ‘path’ attribute signifies the URL or path for which the cookie is valid. The default path attribute is set as ‘/’.
HttpOnly Attribute :
Cookies with the HttpOnly attribute are only accessible via HTTP(S). They are not accessible via JavaScript.
Expires :
The expires attribute indicates the maximum lifetime of the cookie, represented as the date and time at which the cookie expires.
Max-Age :
Recently introduced cookie attribute which serves a similar purpose as of a “Expires’ attribute.
Same Site Attribute :
The Same Site attribute restricts the origin from which the cookie will be sent. Cookie must not be sent with cross-origin requests, providing some protection against cross-site request forgery attacks (CSRF).
Types of Vulnerability
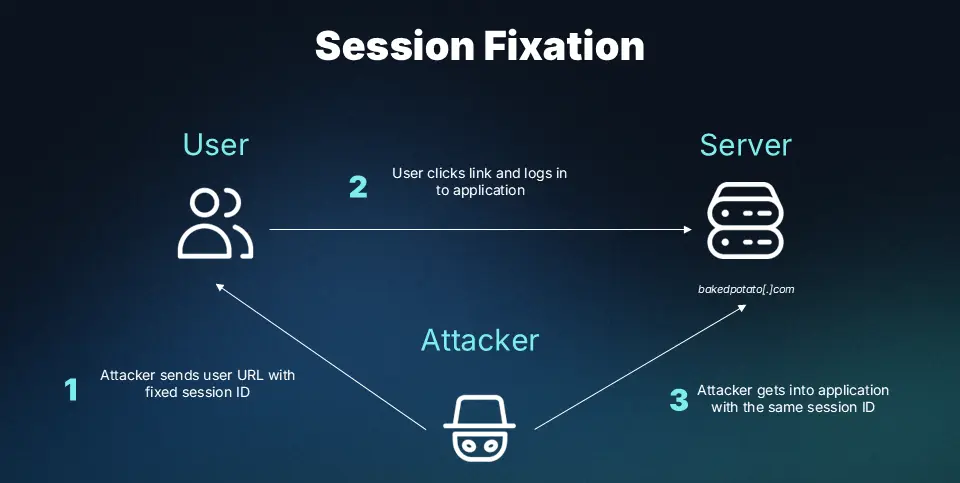
Session Fixation
Session fixation is an attack where an attacker forces a user to use a predetermined session identifier, allowing the attacker to gain control of the victim’s authenticated session after login.
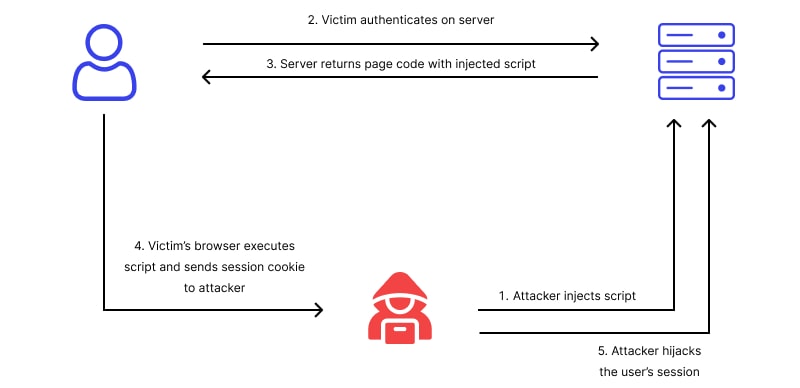
Session Hijacking
Session hijacking is a cyberattack where an attacker gains control of an active session between a user and a web application, allowing them to impersonate the user and access sensitive information without authorization.
Session Timeout/Idle Timeout Issues
Session timeout represents the event occurring when a user does not perform any action on a website during an interval (defined by web server). An attacker can try to steal and use an existing user's session. A long expiration time increases an attacker's chance of successfully guessing a valid session ID. The longer the expiration time, the more concurrent open sessions will exist at any given time.
Improper Session Termination
An attacker can gain access to the resources of a web application that is reserved for other users with the same access rights. Here one user can access other user's account by replacing the session cookie. So this can result in private data leaks of users and one can steal the identity of another user.
What are the Preventions for session management?
- Test for session fixation by setting a session ID before login and checking if it remains the same afterward. Regenerate session IDs upon authentication.
- Always communicate over an encrypted channel (HTTPS).
- Set the Http Only attribute on cookies to prevent access via JavaScript.
- Enable HSTS and ensure the Secure and Domain attributes are correctly configured.
- Set the session timeout in the web.xml file to the minimum recommended value of 30 minutes.
- Set the Secure Flag. Make sure cookies are only sent over HTTPS.
Example:Set-Cookie: sessionid=abc; Secure - Set the HttpOnly Flag. Blocks JavaScript from reading cookies, which helps prevent XSS attacks.
Example:Set-Cookie: sessionid=abc; HttpOnly - Use the SameSite Attribute. Stops cookies from being sent with requests from other websites (helps prevent CSRF).
- Use: SameSite=Strict or SameSite=Lax
- Limit Domain and Path. Only allow cookies on specific domains or paths to reduce exposure.
Example:Domain=example.com; Path=/account


