Broken Access Control & Auth: A Security Breakdown
Broken Access Control and Authentication vulnerabilities are critical security flaws that allow unauthorized users to gain access to restricted areas and sensitive data, posing serious risks to web applications.

Asman

Broken Access Control and flawed Authentication mechanisms are critical security vulnerabilities that can lead to unauthorized access and data breaches. Broken Access Control occurs when users can act outside of their intended permissions—such as accessing another user's data or admin functionalities—due to improperly enforced restrictions. Authentication issues, on the other hand, arise when identity verification mechanisms (like login systems) fail to protect against unauthorized access, often due to weak passwords, session hijacking, or flawed logic. These vulnerabilities can be exploited to gain sensitive information, escalate privileges, or take over accounts. Robust implementation of role-based access controls, secure session management, and multi-factor authentication are essential defenses against these threats.
Difference between Broken Access Control and Broken authentication
Broken access control and broken authentication are distinct web application security vulnerabilities, though related. Broken access control (also known as authorization failure) occurs when an application doesn't properly restrict access to resources based on user roles or permissions, potentially allowing unauthorized users to view, modify, or delete data they shouldn't. Broken authentication (also known as identification and authentication failures) involves weaknesses in the process of verifying a user's identity, allowing attackers to impersonate legitimate users or bypass security measures.
What is Broken access control?
Broken access control is a type of security vulnerability that arises when the access control mechanisms of a system are improperly implemented or enforced. It means that a user is able to perform actions they should not have permission to do. This could allow attackers to gain unauthorized access to sensitive data or functionalities within a system.
For Example, an attacker may be able to exploit a flaw in an application to gain elevated access to data to which they are not entitled and can perform unauthorized actions.
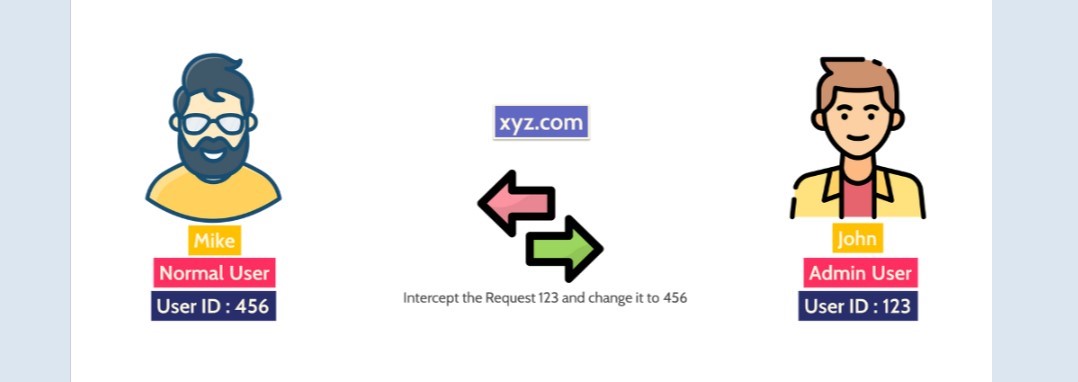
What are access control vulnerabilities?
Access control vulnerabilities occur when an application does not properly enforce what users can access based on their roles or permissions. These vulnerabilities allow unauthorized access, enabling attackers to view, modify, or delete data, perform unauthorized actions, and even escalate privileges.
Common causes include improper implementation of access controls, lack of role validation on the server side, insecure direct object references (IDOR), and trusting client-side controls.
Most common access control Vulnerabilities
Insecure Direct Object References (IDOR)
Insecure Direct Object References (IDOR): This vulnerability occurs when an application uses user-supplied input to directly access an object, such as a file, record, or database key, without proper access control checks. An attacker can manipulate the input to access resources that belong to other users or should not be accessible to them. For example, changing a user ID in a URL to access another user’s account details.
Privilege Escalation
This vulnerability occurs when an attacker is able to exploit a bug or design flaw in an application to gain access to resources or functionality that should be restricted to higher-privileged users. This can involve either Vertical Privilege Escalation (e.g., a normal user gaining administrative privileges) or Horizontal Privilege Escalation (e.g., a user gaining access to another user’s resources at the same privilege level).
Privilege escalation is classified into two types
Horizontal Privilege Escalation :
Horizontal Privilege Escalation is a user level resource escalation technique which allows user “A” to access user “B” data/resources, gaining access to another account with similar rights/authority is know as horizontal privilege escalation. It is also referred as “Account takeover”.
Vertical Privilege Escalation :
Vertical Privilege Escalation involves gaining access to another account with high privilege or moving up forward from “Low” privileged account to “High” privileged account.
Parameter Tampering
Parameter tampering is a vulnerability which occurs when an application does not validate the user supplied input or gives access to a particular resource by just modifying the values.
Failure to enforce Business Login Access Control
Failing to restrict URL access happens when a page doesn’t have the correct access control policy in place. Unauthorized users are able to view content that they shouldn’t have the ability to view.
What are the preventive measures?
Do Not Rely on Obfuscation :
Obfuscation is not sufficient for keeping sensitive information safe.
Deny Access by Default :
Unless a resource is intended to be publicly accessible, deny access by default. Design an effective access control. Furthermore, at the code level, make it mandatory for developers to declare the access that is allowed for each resource, and deny access by default.
Set proper permissions or use Access Control Lists (ACLs) to prevent anonymous users from reading files or data they shouldn't see.
Never allow anonymous web visitors to have read access to sensitive or private files.
Use a role-based access control (RBAC) policy, so each user only has access to what their role requires—nothing more.
What is Broken Authentication?
Broken authentication occurs when authentication mechanisms are improperly implemented, allowing attackers to bypass or exploit them. This can happen due to weak password policies, poor session management, insecure storage of credentials, and more. Broken authentication is listed as one of the top security risks in the OWASP Top 10.
For example, attackers may be able to exploit identification and authentication failures by compromising passwords, keys session tokens, or exploit other implementation flaws to assume other user identities.
What are authentication vulnerabilities?
Authentication vulnerabilities are problems with the way a website or app checks who you are (like when you log in with a username and password). These problems can let hackers break in and pretend to be someone else.
Most vulnerabilities in authentication mechanisms occur in one of two ways:
Weak protection against guessing
If the system doesn’t stop people from trying lots of passwords quickly (called a brute-force attack), a hacker might guess the right one eventually.
Logic flaws or poor coding
If the code that checks logins has errors (called logic flaws), a hacker might be able to trick the system into letting them in without knowing the correct password. This is known as broken authentication.
Most common Authentication Vulnerabilities
Phishing Attacks
Credential Stuffing
Weak Passwords
Insecure Authentication Protocols
Brute Force Attacks
Session Hijacking
Lack of Multi-Factor Authentication
What are the preventive measures?
Implement Multi-Factor Authentication (MFA) :
MFA adds an extra layer of security by requiring users to provide multiple forms of identification, reducing the risk of unauthorized access.
Enforce Secure Password Policies :
Implement strong password requirements and disallow the use of weak or common passwords to enhance authentication security.
Protect Session IDs :
Ensure that session IDs, such as cookies or tokens, are safeguarded and rotated after successful logins to prevent session hijacking.
Session Management :
Properly invalidate session IDs during logout or inactivity and enforce secure session management practices to mitigate authentication vulnerabilities.
Use Secure Frameworks and Libraries :
Employ community-vetted frameworks, libraries, and secure coding patterns to embed robust authentication mechanisms in software applications.
Regular Security Audit :
Conduct regular security audits to identify and address any vulnerabilities in the authentication process.


