Reconnaissance Techniques in Penetration Testing: A Hands-On Approach
Reconnaissance, also referred to as foot printing, is the initial phase of ethical hacking. During this stage, pentesters collect information about a target system, application, or organization to identify potential vulnerabilities and attack surfaces. The goal is to build a detailed profile of the target using both passive and active techniques. This intelligence helps guide and prepare for the next phases of penetration testing by revealing weaknesses that could be exploited.

Asman

Types of Reconnaissance
Reconnaissance in ethical hacking is divided into two main categories based on the method of information gathering:
1. Passive Reconnaissance
Passive reconnaissance focuses on collecting data from publicly accessible sources without alerting the target.
Key Methods:
- OSINT (Open-Source Intelligence) Utilizing publicly available information such as social media profiles, job postings, and news articles.
- WHOIS Lookup: Gathering details about domain registrations, including ownership and contact information.
- Social Engineering: Observing publicly shared details that could be leveraged in attacks.
Popular Tools for Passive Reconnaissance:
- Maltego: Visualizes relationships between data points.
- Recon-ng: A modular framework for gathering OSINT.
- Shodan: A search engine for internet-connected devices.
- Google Dorks: Advanced search queries to find hidden information.
2. Active Reconnaissance
Active reconnaissance involves directly engaging with the target system to gather in-depth and precise information.
Common Techniques:
- Network Scanning: Detects active devices, open ports, and available services using tools like Nmap.
- DNS Interrogation: Gathers DNS records (A, MX, TXT, etc.) to learn more about domain configurations.
- Banner Grabbing: Retrieves service banners to identify software types and versions.
Popular Tools for Active Reconnaissance:
- Nmap: Comprehensive tool for scanning networks and discovering hosts and services.
- Netcat: Versatile utility for testing and interacting with open ports.
- Metasploit Framework: A powerful platform for vulnerability assessment and exploitation.
- Dig & Nslookup: Command-line utilities for performing DNS lookups and extracting domain-related data.
Why is Information Gathering Important?
- 1. Understanding the Attack Surface: Identifying potential entry points that attackers could exploit.
- 2. Improved Risk Assessment: Gaining insights into vulnerabilities and threats specific to the target environment.
- 3. Enhanced Defence Strategies: Crafting targeted measures to mitigate identified risks.
- 4. Legal and Ethical Investigations: Supporting ethical hacking, penetration testing, and digital forensics.
Methods of Reconnaissance
Reconnaissance is the initial phase of pen testers or penetration testing, focused on gathering information about the target system or network. It is broadly classified into passive and active reconnaissance. Below are the key methods involved in this phase:
1. Network Mapping
Network mapping is the process of visually or logically representing the structure of a target network, including connected devices, servers, and communication paths.
Purpose:
To understand the layout and topology of a network, which helps in identifying key assets and potential entry points.
Common Tools:
- Nmap (with Zenmap for GUI visualization)
- SolarWinds Network Topology Mapper
- NetBrain
- 4. Legal and Ethical Investigations:
2. Footprinting
Foot printing involves gathering publicly available information about a target organization to create a detailed profile.
Purpose:
To identify domain names, IP ranges, external systems, and other public infrastructure components.
Common Techniques & Tools:
- WHOIS Lookup (e.g., whois example.com)
- Google Dorking (e.g., site:example.com filetype:pdf)
- DNS Enumeration using tools like Fierce or DNSRecon
3. Scanning
Scanning is the process of probing a system or network to discover open ports, running services, and potential vulnerabilities.
Purpose:
To find weak points in a system that can be exploited in later stages.
Common Techniques:
- Port Scanning Identifying open ports.
- Service Detection Finding out which services are running and their versions.
- Vulnerability Scanning Detecting known vulnerabilities.
Popular Tools:
- Nmap
- OpenVAS
- Nessus
4. Enumeration
Enumeration involves active interaction with the target system to extract detailed information such as usernames, network shares, and configuration data.
Purpose:
To gain deeper insight into the target's internal structure and potential access points.
Common Techniques:
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Queries
- SMTP VRFY command
Popular Tools:
- Enum4linux
- SNMPWalk
- Nmap NSE Scripts
Tools and Technologies Used for Reconnaissance
- WHOIS
- VirusTotal
- Wayback Machine
- Hunter.IO
- MX toolbox
- DNSChecker
- Shodan.io
- Ping
- Nmap
- Wappalyzer
- Url Fuzzer
WHOIS:
WHOIS is a widely used Internet record listing that identifies who owns a domain and how to get in contact with it. The Internet Corporation for Assigned Names and Numbers (ICANN) regulates domain name registration and ownership. Who is records have proven to be extremely useful and have developed into an essential resource for maintaining the integrity of the domain name registration and website ownership process.
VirusTotal:
VirusTotal was founded in 2004 as a free service that analyzes files and URLs for viruses, worms, trojans, and other kinds of malicious content. Our goal is to make the internet a safer place through collaboration between members of the antivirus industry, researchers, and end users of all kinds.
Wayback Machine:
The Internet Archive Wayback Machine is a service that allows people to visit archived versions of Web sites. Visitors to the Wayback Machine can type in a URL, select a date range, and then begin surfing on an archived version of the Web.
Hunter.IO:
Hunter.IO is an online service that offers various services for finding emails by name or phone number. It’s one of several similar services like Gmail Finder which can help you find your lost emails easily.
MX toolbox:
MxToolbox supports global Internet operations by providing free, fast, and accurate network diagnostic and lookup tools. Millions of technology professionals use our tools to help diagnose and resolve a wide range of infrastructure issues.
DNSchecker:
DNSChecker is a free service providing users with fast and reliable DNS services, email-related lookups, and IP-related services for more than ten years.
Shodan.io:
Shodan is a search engine that lets users search for various types of servers (webcams, routers, servers, etc.) connected to the internet using a variety of filters. Some have also described it as a search engine for service banners, which are metadata that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message, or anything else that the client can find out before interacting with the server.
Ping:
A ping (Packet Internet or Inter-Network Groper) is a basic Internet program that allows a user to test and verify if a particular destination IP address exists and can accept requests in computer network administration.
WhatWeb:
The WhatWeb is a tool that is used to identify different web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices.
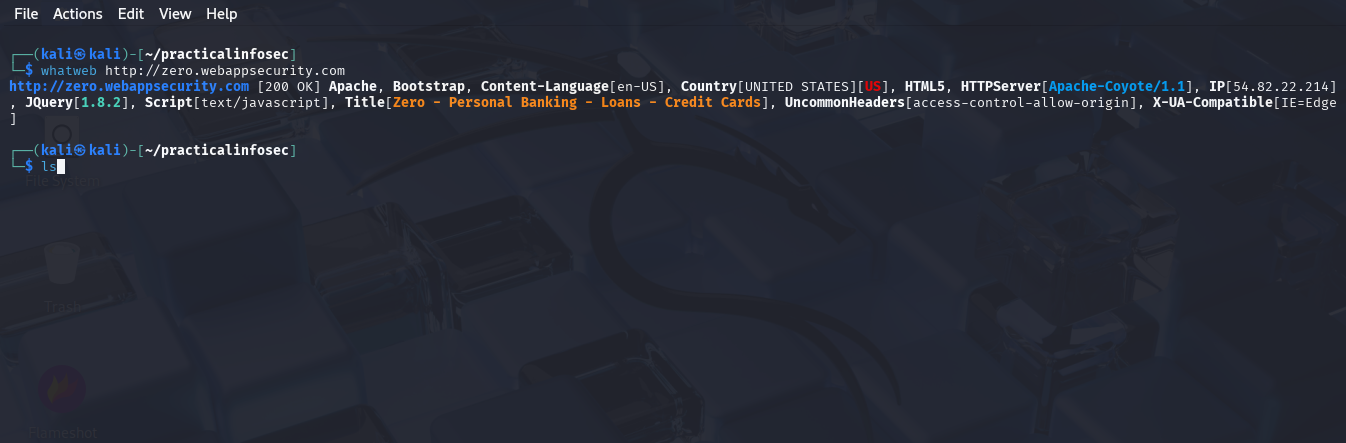
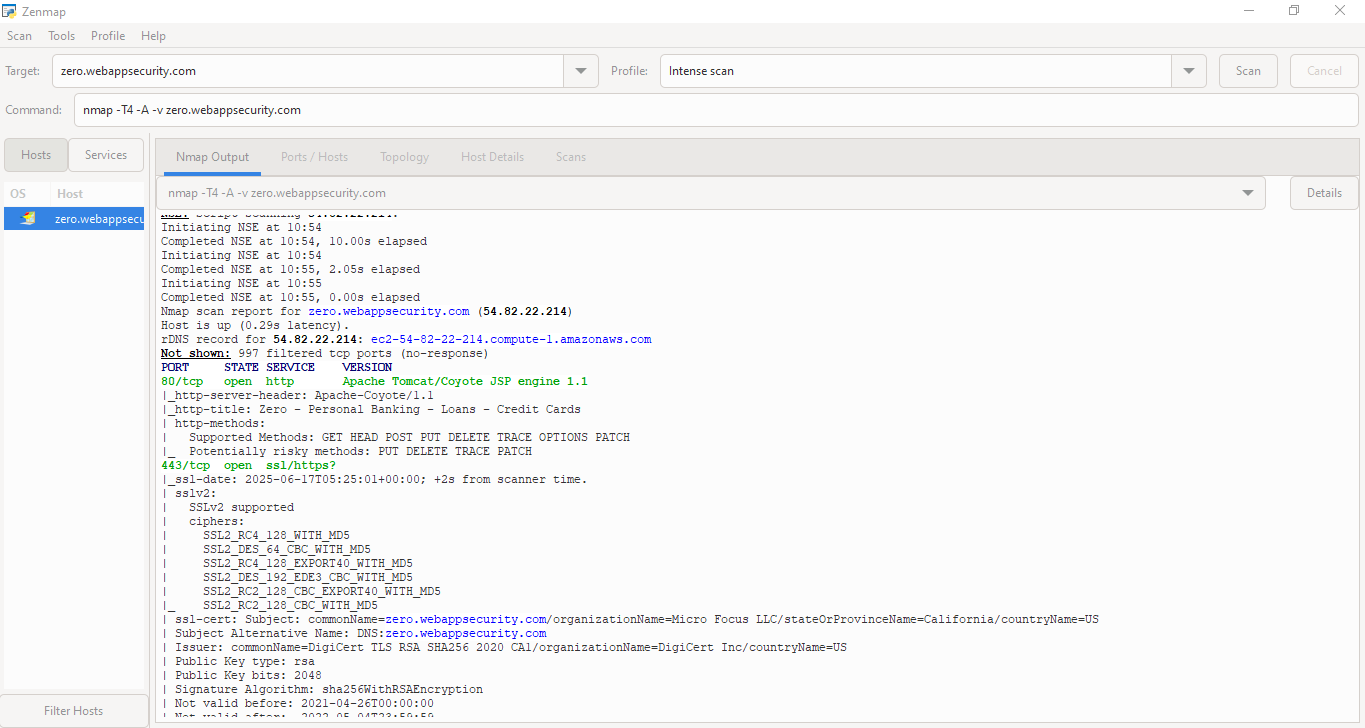
Nmap:
Nmap (“Network Mapper”) is an open-source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts.
Wappalyzer
Wappalyzer is a technology profiler used to extract information related to the technology stack of the target. If you want to find out what CMS or libraries the target is using and any framework, Wappalyzer is the tool to use.
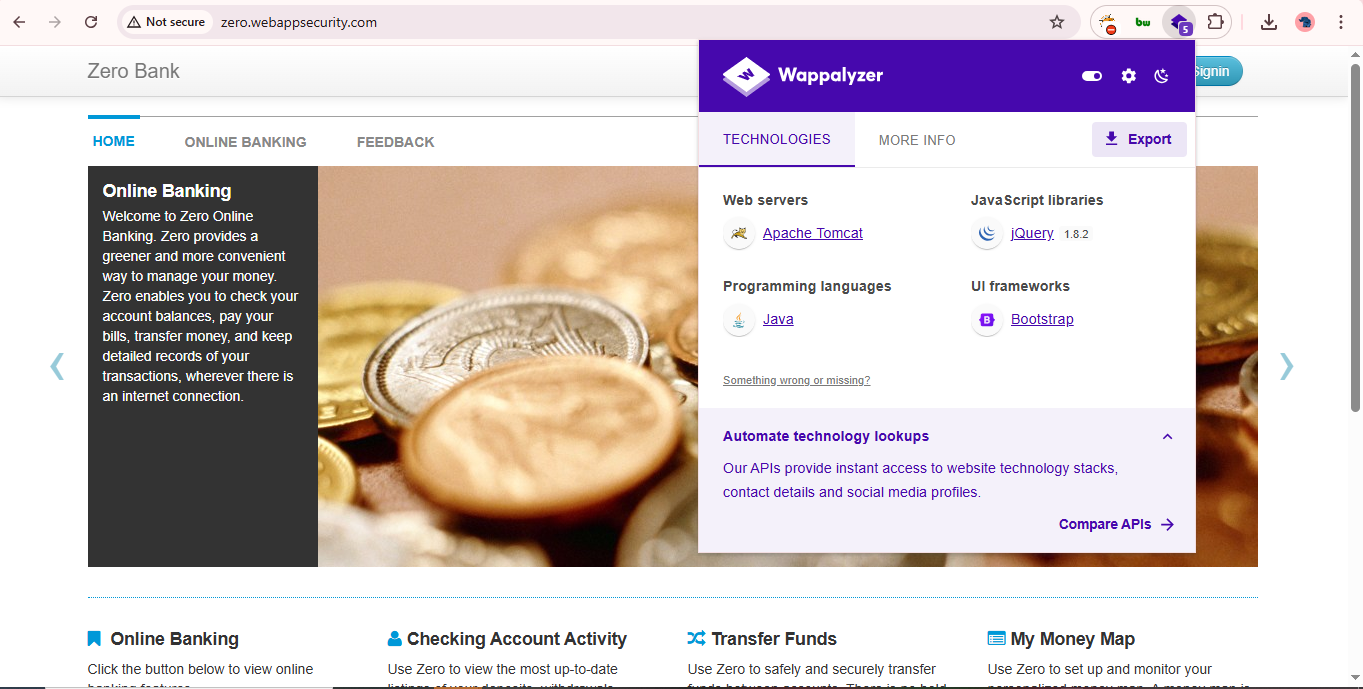
There are different ways to use it — you can access information on the target by using the Lookup API. This method is mostly used by security engineers or InfoSec developers to integrate Wappalyzer as a technology profiler in a security product. Otherwise, you can install Wappalyzer as a browser extension for Chrome, Firefox, and Edge.
Find Folders and Files
It is important to know which type of files or folders are hosted on the target web server in a pentest project. You will usually find sensitive information in files and folders such as administrator password, GitHub key, and so on a web server.
URL Fuzzer:
Url Fuzzer is an online service by Pentest-Tools. It uses a custom-built wordlist for discovering hidden files and directories. The wordlist contains more than 1000 common names of known files and directories.
It allows you to scan for hidden resources via a light scan or full scan. The full scan mode is only for registered users.
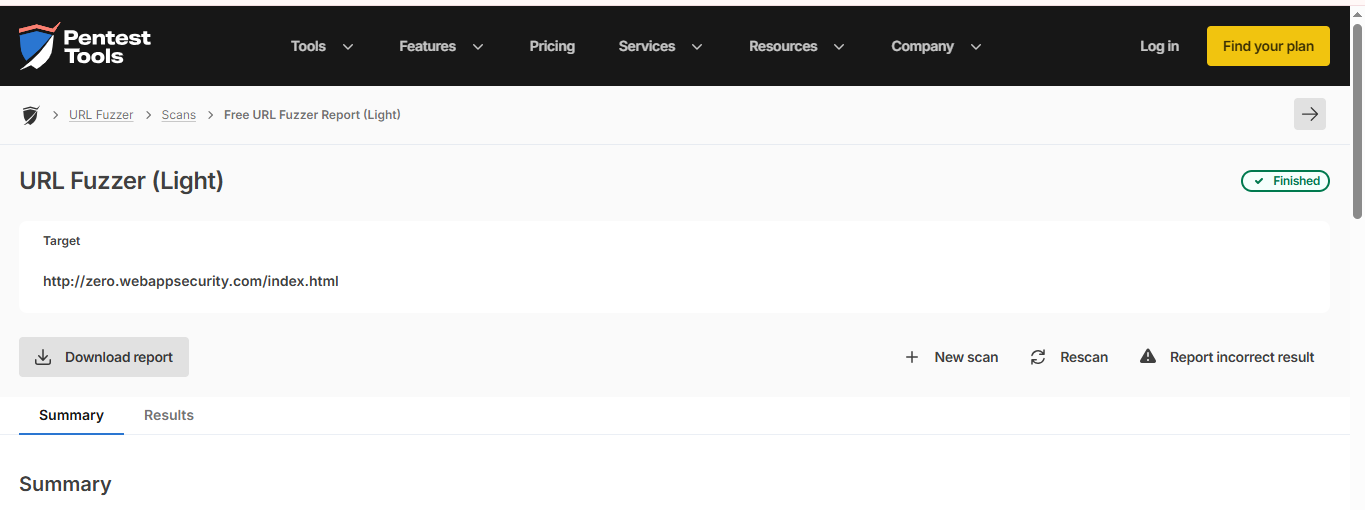
Pentest Tools got more than 20 tools for information gathering, website security testing, infrastructure scanning, and exploit helpers.
Conclusion:
Information gathering is an art that every penetration-tester (pen-tester) and hacker should master for a better experience in penetration testing. It is a method used by analysts to determine the needs of customers and users.


