Understanding SQL Injection: A Web Security Threat
SQL Injection is a serious web security flaw that lets attackers manipulate SQL queries to access or alter database data. It can lead to data breaches, loss, or full database control if not properly prevented. Let's get started!

Asman
Understanding SQL Injection
SQL injection involves exploiting input fields in a web application to execute unauthorized SQL commands. When an application fails to properly validate or sanitize user input before building SQL queries, attackers can inject malicious SQL code. This can lead to unauthorized access, data exfiltration, modification, or even deletion of entire datasets—ultimately allowing the attacker to manipulate the database in unintended and potentially damaging ways.
SQL injection occurs when an attacker inserts malicious SQL code into input fields of a web application—such as search boxes, login forms, or contact pages. This vulnerability poses a serious threat, as it can lead to the theft of sensitive data, unauthorized access, and even full system compromise. It remains a common and dangerous attack vector, consistently ranking among the top threats in OWASP’s Top 10 Application Security Risks, where SQL injection is listed as the second most critical vulnerability.
What is SQL queries in a database?
SQL (Structured Query Language) is the standard programming language used for managing and manipulating data in a Relational Database Management System (RDBMS) or in stream processing within a Relational Data Stream Management System (RDSMS). Put, SQL is a declarative language that enables users to store, retrieve, update, delete, and manage data in relational databases.
SQL queries are structured commands written in SQL to interact with databases. They allow users to perform a wide variety of operations, including retrieving specific records, modifying existing data, adding new entries, or removing outdated ones.
Some key functions SQL queries can perform include:
- Retrieving data from a database
- Inserting, updating, or deleting records
- Creating new databases and tables
- Defining stored procedures and views
- Setting user permissions on tables, views, and procedures
SQL commands are typically structured as statements and can be combined into full programs or scripts to carry out complex operations on data.
A few basic examples of SQL queries include:
SELECT: Intended to retrieve data from tables.
SELECT column1, column2 FROM tablename WHERE condition;
INSERT INTO: Intended to insert new data into a table.
INSERT INTO tablename (column1, column2) VALUES (value1, value2);
UPDATE: Intended to modify existing data in a table.
UPDATE tablename SET column1=value1 WHERE condition;
Different types of SQL injection
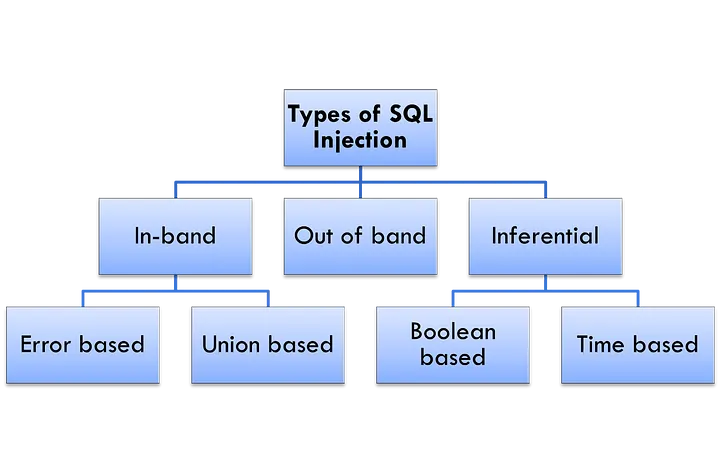
1.In-Band SQLi:
The attackers use the same communication channel to launch their attacks and collect results.
Error Based
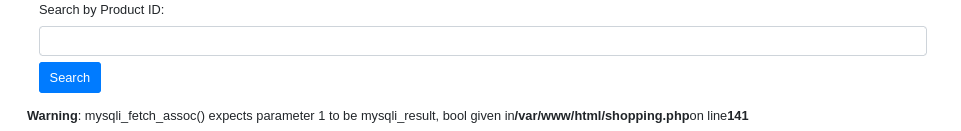
Error-based SQL injection is a type of SQL injection attack where the attacker exploits error messages generated by the database server to gather information about the structure of the database or to extract data.
Example :

The error is dependent upon the kind of database used in the backend, given below is an example.
Union Based
In this technique, the UNION SQL operator is used to combine the results of two or more SELECT statements into a single HTTP response. Attackers can craft these queries directly within the URL or input fields to manipulate the query and retrieve additional data from the database.
Example
Steps to exploit Union Based SQL Injection
- 1. Determine number of columns that the query is making while supplying user input
- 2. Figure out the data types of the columns (string datatype is common and helpful)
- 3. Utilize UNION operator to extract sensitive information from the database
- Defining stored procedures and views
- Setting user permissions on tables, views, and procedures
https://example.com/products?id=1
https://example.com/products?id=1' order by 1--
https://example.com/products?id=1' order by 2--
https://example.com/products?id=1' order by 3-- # Got error here
https://example.com/products?id=1' UNION SELECT 'a', NULL--
https://example.com/products?id=1' UNION SELECT NULL, 'a'--
https://example.com/products?id=1' UNION SELECT email,pass from users--
2.Blind SQL Injection:
Here, it does not transfer the data via the web application. The attacker can not see the result of an attack in-band.
Boolean Based
In this method, the attacker sends SQL queries that trigger different responses based on whether the query evaluates to true or false. By observing the application's behavior, the attacker can infer information about the database.
Example :
https://example.com/products?name=laptop' AND 1=1
https://example.com/products?name=laptop' AND 1=2
Time-based SQL Injection :
In this technique, the attacker sends SQL queries that cause the database to delay its response by a specific amount of time if a condition is true. The attacker then uses the delay (or lack thereof) to determine whether the injected condition is true or false, helping to extract information from the database without visible output.
Example:
MySQL: SELECT SLEEP(10)
Microsoft: WAITFOR DELAY '0:0:10'
Oracle: dbms_pipe.receive_message(('a'),10)
PostgreSQL: SELECT pg_sleep(10)
3. SQL Injection — Out-of-Band
Out-of-band SQL injection is a type of SQL injection attack that leverages alternative communication channels to exfiltrate data from the target database when direct retrieval through the application’s response is not feasible. This method is particularly useful when traditional SQL injection techniques, such as error-based or time-based attacks, are not effective due to restrictions in the environment or countermeasures implemented by the defender.
Most Common Payloads of SQL injection
- ' OR 1=1 --
- ' OR '1'='1' --
- admin' --
- ' OR 1=1#
Impacts of SQL Injection
Database Enumeration
Attackers can discover details about the database structure, such as table names, column names, and data types. This is often done using error messages or blind injection techniques like time delays or Boolean logic.
Privilege Escalation
If user role data is exposed, attackers can identify high-privilege accounts like database admins or application superusers. This can lead to elevated access, allowing further compromise of the system.
Stealing credentials:
SQL injections can be used to obtain users’ credentials. Attackers can access their privileges then pose as these users.
Accessing database:
Attackers can use SQL injections to reach information stored in a database server.
Altering data:
Attackers can use SQL injections to modify or destroy the accessed database.
Accessing networks:
Attackers can use SQL injections to reach information stored in a database server.
Accessing database:
Attackers can use SQL injections to access database servers with operating system privileges. Then, the attacker can try to access the network.
Prevention for SQL Injection
Use Parameterized Queries:
Separate SQL logic from user input to prevent malicious code injection.
Validate Input:
Ensure all user input is checked for expected format and type before processing.
Escape User Input:
Properly encode special characters to neutralize potentially harmful input.
Limit Database Privileges:
Grant only necessary permissions to reduce impact if a breach occurs.
Avoid Shared Database Accounts:
Use unique, restricted accounts for each application or website.
Keep Software Updated:
Apply security patches regularly to close known vulnerabilities.


